The Lighthouse: CIP low impact from the ground up – Part 8.2, Developing your physical security controls plan
 By Lew Folkerth, Principal Reliability Consultant, External Affairs
By Lew Folkerth, Principal Reliability Consultant, External Affairs
In this recurring column, I explore various questions and concerns related to the NERC Critical Infrastructure Protection (CIP) Standards. I share my views and opinions with you, which are not binding. Rather, this information is intended to provoke discussion within your entity. It may also help you and your entity as you strive to improve your compliance posture and work toward continuous improvement in the reliability, security, resilience and sustainability of your CIP compliance programs. There are times that I also may discuss areas of the standards that other entities may be struggling with and share my ideas to overcome their known issues. As with lighthouses, I can’t steer your ship for you, but perhaps I can help shed light on the sometimes-stormy waters of CIP compliance.
Photo: Big Sable Point Lighthouse, Michigan (Lew Folkerth)
NERC Reliability Standard CIP-003-9 (Security Management Controls) Requirement R2 requires implementation of cyber security plans for low impact BES Cyber Systems. Requirement R2 calls Attachment 1 of the standard into scope, which is where the detailed plan requirements, broken into six sections, reside. I will cover each of these sections in-depth as part of this series.
Section 2 of CIP-003-9 Attachment 1 covers physical security controls. It states:
“Each Responsible Entity shall control physical access, based on need as determined by the Responsible Entity, to (1) the asset or the locations of the low impact BES Cyber Systems within the asset, and (2) the Cyber Asset(s), as specified by the Responsible Entity, that provide electronic access control(s) implemented for Section 3.1, if any. ”
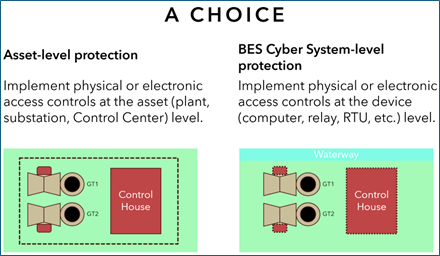
Figure 1
The essence of Section 2 is the control of physical access. This implies that monitoring of physical access, while good practice, is not in itself sufficient to meet compliance. You have the option of controlling access to the entire asset, or to only the locations of the BES Cyber Systems and the firewall (or other electronic access control device) within the asset.
This choice in approach you will make on a physical-asset-by-physical-asset basis. For example, you might choose to protect the low impact BES Cyber Systems (and firewall) at generating plant XYZ and protect the entire physical asset at substation QRP.
If you choose the Cyber Asset-based approach, you will need to have a list of those Cyber Assets (BES Cyber Systems) for an audit team to review. In other words, if you don’t have the list of Cyber Assets you must protect, then you will need to protect all Cyber Assets at the physical asset.
The four D’s
Before we discuss Section 2 in detail, let’s look at the conceptual foundation of physical security, the “Four D’s” (see Figure 2)¹:

Figure 2 (Source: ChatGPT-generated image from a Copilot prompt by Lew Folkerth)
- Deter
Ideally, your asset’s physical protective measures will appear so formidable that an intruder will not even attempt an intrusion. - Detect
Response to an intrusion begins with the detection of the intrusion. This implies monitoring of the asset perimeter, such that the beginning of an intrusion is signaled by camera, motion detector, or other means. - Delay
A successful security program must delay an intruder for the time required for defensive response. This can be accomplished by fences, walls, locks, etc. - Defend (Deny, Respond)
Defense of an asset is usually accomplished by a physical response, such as law enforcement or security personnel.
As you can see, Section 2 only addresses part of a complete physical security plan. That’s because Section 2 is focused on protecting cyber systems, not the entire physical asset at which the cyber systems are located. At present, only CIP-014 (Physical Security) addresses a full range of physical security for physical assets, and then only for a small subset of physical assets.
As you develop your Section 2 plan, I recommend you consider designing and implementing a full set of physical protections in addition to the required access controls. You can learn more about this at SERC University. For example, look for a course with the title, “GridSecure: Physical Security Workshop,” which is a three-day workshop focusing on physical security for electric sector assets. I’ve taken this class, and I can highly recommend it.
Controlling physical access
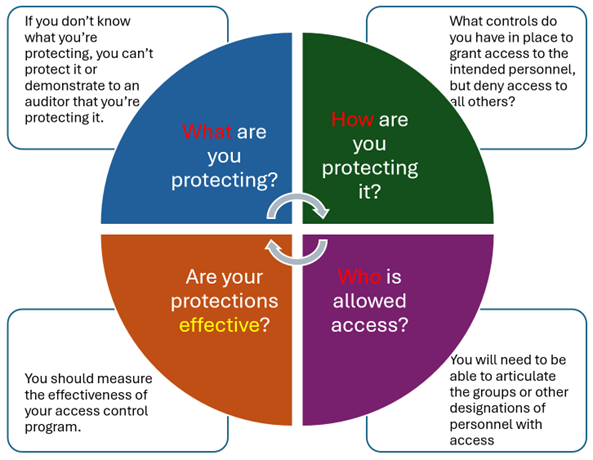
Figure 3
In my opinion, controlling physical access has multiple components (see Figure 3):
- You must know what you’re protecting with your access controls
- You must know how you’re protecting it
- You must know who will have access
- You should measure the effectiveness of your controls
Since you must control physical access, this also implies that you need some form of authentication. Authentication doesn’t need to be at the individual level, it may also be done at a group level.
Controlling physical access can be a problem with field assets, such as solar generation. From what I’ve seen, the solar-powered inverters on the market may permit physical access to the network of the BES Cyber System controlling the inverter. If this is the case, you may need to implement alternate means of protecting the BES Cyber System. This could include a fence with locking gate around the inverter, a port lock on the inverter, or another means of controlling access to the inverter. Keep in mind the difficulties in relying on the asset’s perimeter fence, where farmers or other land maintenance personnel may need unrestricted access.
In summary, when it comes to Section 2 of CIP-003-9 Attachment 1, here’s what you must do:
• Develop, document and implement a plan to control physical access to either the entire physical asset or the location of the BES Cyber Systems and firewall within the physical asset. The decision of whether to protect the entire physical asset or each individual BES Cyber System (and access control device) can be determined independently for each physical asset. Note that a documented Physical Security Perimeter is not necessary at the low impact level (but see below).
And here’s what you should do:
• Implement an identity and authorization management (IAM) program so you know who is allowed access to your physical assets and why the access is needed. Your IAM program should include a periodic review to ensure all access authorizations are current.
• Consider implementing layered access controls to your physical assets. For example, a perimeter fence could be supplemented with access protections such as locked cabinets or a locked control house at an unstaffed site.
• Document the perimeter, including all access points, location and type of locks/authentication mechanisms, location and type of monitoring, types of alarming, and any other protective measures.
• Conduct periodic physical walkdowns of each site to ensure all necessary protections are in place.
• Periodically review the effectiveness of your protection mechanisms. For example, if you use physical locks, research the type of lock you are using to determine whether there is a bypass method available. Locks used on your physical assets should not be easy to bypass.
• Periodically review the effectiveness of monitoring systems used to supplement your physical access controls.
• Periodically review the use of lighting as a deterrent to unauthorized physical access.
• Develop and periodically exercise a physical incident response plan. This will be different from the cyber security incident response plan required by Section 4.
• Periodically conduct physical penetration testing. This will let you work out how long the delay is from detection to response, and what an attacker can accomplish in that time.
• As I write this, a Reliability and Security Technical Committee (RSTC) subgroup is working on a guideline, Voluntary Physical Security Protection Best Practices at BPS Facilities. Keep an eye on the Security Guidelines webpage. When the guideline is published, I suggest you read it and consider implementing any appropriate measures.
I’ll cover Sections 3-6 of CIP-003-9 Attachment 1 in forthcoming issues of The Lighthouse: CIP Low Impact from the Ground Up series.
Footnotes:
- Adapted from Protection of Assets, ASIS International, 2021

