The Lighthouse: CIP low impact from the ground up – Part 8, Developing your low impact cyber security plans
 By Lew Folkerth, Principal Reliability Consultant, External Affairs
By Lew Folkerth, Principal Reliability Consultant, External Affairs
In this recurring column, I explore various questions and concerns related to the NERC Critical Infrastructure Protection (CIP) Standards. I share my views and opinions with you, which are not binding. Rather, this information is intended to provoke discussion within your entity. It may also help you and your entity as you strive to improve your compliance posture and work toward continuous improvement in the reliability, security, resilience and sustainability of your CIP compliance programs. There are times that I also may discuss areas of the standards that other entities may be struggling with and share my ideas to overcome their known issues. As with lighthouses, I can’t steer your ship for you, but perhaps I can help shed light on the sometimes-stormy waters of CIP compliance.
Photo: Marquette Harbor Lighthouse, Marquette, Michigan (Lew Folkerth)
NERC Reliability Standard CIP-003-9 (Security Management Controls) Requirement R2 requires implementation of cyber security plans for low impact BES Cyber Systems. CIP-003-9 will become effective April 1, 2026, so you need to be preparing for it now. Here’s what Requirement R2 says:
“CIP-003-9 R2. Each Responsible Entity with at least one asset identified in CIP‐002 containing low impact BES Cyber Systems shall implement one or more documented cybersecurity plan(s) for its low impact BES Cyber Systems that include the sections in Attachment 1.
Note: An inventory, list, or discrete identification of low impact BES Cyber Systems or their BES Cyber Assets is not required. Lists of authorized users are not required.”
Requirement R2 calls Attachment 1 of the standard into scope, which is where the detailed plan requirements, broken into six sections, reside. I will cover each of these sections in-depth in mini articles as part of this series. They include:
Section 1. Cyber security awareness
Section 2. Physical security controls
Section 3. Electronic access controls
Section 4. Cyber security incident response
Section 5. Transient cyber asset and removable media malicious code risk mitigation
Section 6. Vendor electronic remote access security controls
CIP-003-9 gives you great flexibility in how you organize your cyber security plans for your low impact physical assets. You may have one plan per section per physical asset. You may cover multiple sections in one plan. You may cover multiple physical assets in one plan. You may use plans for your medium or high impact physical assets at the low impact level. It’s up to you. Per Attachment 1:
“CIP-003-9 Attachment 1. Responsible Entities shall include each of the sections provided below in the cyber security plan(s) required under Requirement R2.
Responsible Entities with multiple‐impact BES Cyber Systems ratings can utilize policies, procedures, and processes for their high or medium impact BES Cyber Systems to fulfill the sections for the development of low impact cyber security plan(s). Each Responsible Entity can develop a cyber security plan(s) either by individual asset or groups of assets.”
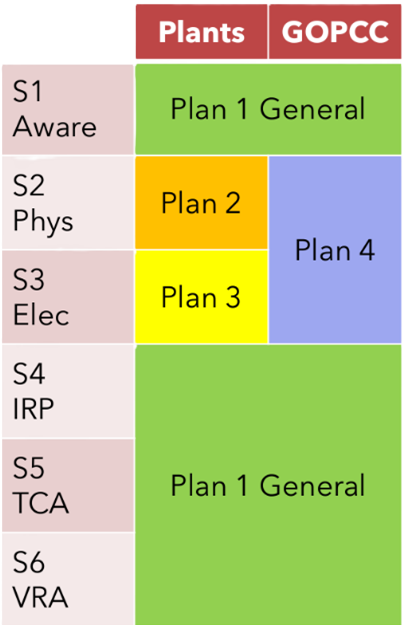
Figure 1. Notional low impact plan organization example
Figure 1 gives an example of one possible cyber security plan organization for an entity registered as a GO/GOP. The “Plants” column shows the plans used for the generating plants, and the “GOPCC” column shows the plans used for the operating Control Centers. Plan 1 covers Attachment 1 Sections 1, 4, 5, and 6 for generating plants and Control Centers. For the generating plants only, Plan 2 covers physical access controls and Plan 3 covers electronic access controls. Plan 4 covers both physical and electronic access controls for Control Centers. Again, this is an example – organize your plans in whatever manner you choose.
What you must do:
→ Create and document a cyber security plan for each of the six sections of CIP-003-9 R2 Attachment 1 for each physical asset identified in CIP-002-5.1a (Cyber Security — BES Cyber System Categorization) R1.3 as containing a low impact BES Cyber System.
What you should do:
→ Periodically (perhaps annually?) review your cyber security plans for your low impact BES Cyber Systems to ensure each physical asset containing low impact BES Cyber Systems has an applicable cyber security plan for each of the six sections of CIP-003-9 Attachment 1.
Next, we’ll dive into Sections 1-6 of Attachment 1 in more detail, starting with Section 1: Cyber security awareness.

