The Lighthouse: Quantum computing and operational systems
 By Lew Folkerth, Principal Reliability Consultant, External Affairs
By Lew Folkerth, Principal Reliability Consultant, External Affairs
In this recurring column, I explore various questions and concerns related to the NERC Critical Infrastructure Protection (CIP) Standards. I share my views and opinions with you, which are not binding. Rather, this information is intended to provoke discussion within your entity. It may also help you and your entity as you strive to improve your compliance posture and work toward continuous improvement in the reliability, security, resilience and sustainability of your CIP compliance programs. There are times that I also may discuss areas of the standards that other entities may be struggling with and share my ideas to overcome their known issues. As with lighthouses, I can’t steer your ship for you, but perhaps I can help shed light on the sometimes-stormy waters of CIP compliance.
Photo: McGulpin Point Lighthouse (Lew Folkerth)
Secrets
Think of a world where there are no secrets. Anything you write, say, or do can be intercepted and understood by anyone. Your phone calls, emails and messaging are public for anyone to read. Your bank account and credit cards are all accessible by anyone. Your online activities including shopping, entertainment and education are an open book. Your organization’s information is available to anyone. Its intellectual property, finances and strategic documents are public. Personnel issues, hiring and firing are known by anyone interested.
That is the world we might live in if we didn’t have cryptography.
Cryptography plays a role in our lives every day, but we seldom see it because it is hidden behind the scenes. And several of the types of cryptography we use without knowing it are threatened by computing advances that are on the horizon.
In this article I’ll explore what’s coming in cryptography, how it affects cyber security in our operational systems, and how to begin preparing for these changes.
Cryptography
Cryptography, in the broadest sense, is the art and science of controlling access to information by mathematical methods. When we use cryptography, mathematical techniques to protect information, we are said to be encrypting that information. When we reverse the encryption to be able to read the protected information, we are decrypting that information. Modern cryptography uses two general types of encryption, symmetric and asymmetric.
Symmetric cryptography
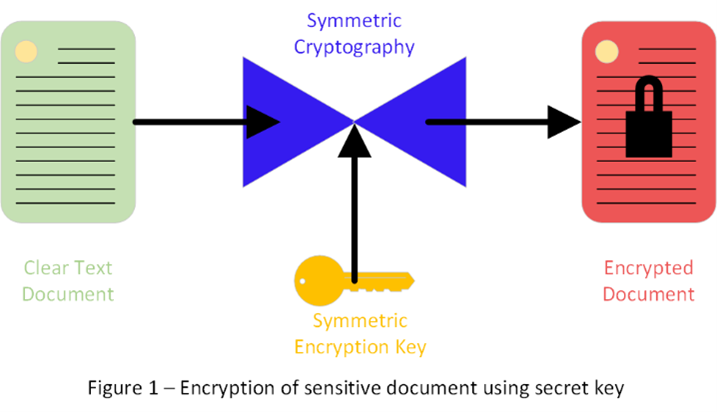 Probably the simplest use of cryptography is to protect a secret from unauthorized disclosure. To do so, you would take the computer file containing the secret and pass it through an encryption program (see Figure 1). The encryption program will ask you for a key to encrypt the file. The result is an encrypted file that cannot be read without the key. To decrypt the file, you will perform the same sequence of steps but this time you will feed the encrypted file into the encryption program and use the same key you used in the initial encryption (see Figure 2).
Probably the simplest use of cryptography is to protect a secret from unauthorized disclosure. To do so, you would take the computer file containing the secret and pass it through an encryption program (see Figure 1). The encryption program will ask you for a key to encrypt the file. The result is an encrypted file that cannot be read without the key. To decrypt the file, you will perform the same sequence of steps but this time you will feed the encrypted file into the encryption program and use the same key you used in the initial encryption (see Figure 2).
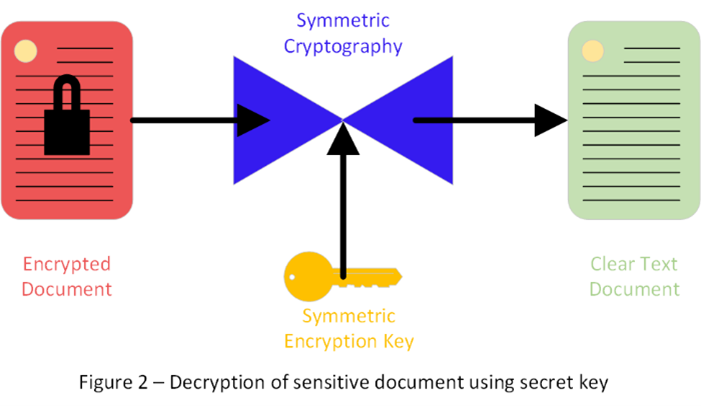 You use the encryption program with your key once to encrypt the file, and the same program and key a second time to decrypt the file. This is where symmetric encryption gets its name; you are using the same program and key to both encrypt and decrypt your information. The strength of the encryption depends on the quality of the mathematical function used by the encryption program, the size of the key, and the strength (i.e., the ability of an adversary to guess the key) of the key. If you make good choices for these encryption elements, and keep the key safe, your secret is secure.
You use the encryption program with your key once to encrypt the file, and the same program and key a second time to decrypt the file. This is where symmetric encryption gets its name; you are using the same program and key to both encrypt and decrypt your information. The strength of the encryption depends on the quality of the mathematical function used by the encryption program, the size of the key, and the strength (i.e., the ability of an adversary to guess the key) of the key. If you make good choices for these encryption elements, and keep the key safe, your secret is secure.
You can send the resulting encrypted file by any chosen communication method and be sure that no one who might intercept the file can read it without the encryption key. But your intended recipient needs your encryption key to be able to read the file. Asymmetric encryption solves that problem.
 Asymmetric cryptography
Asymmetric cryptography
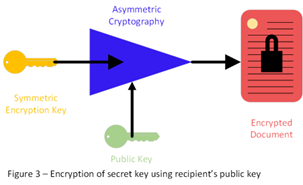
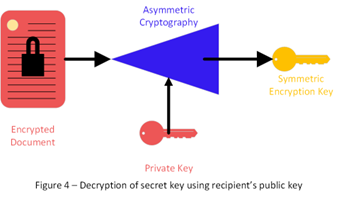
Asymmetric cryptography uses two keys, a public key and a private key. You keep the private key secret and can publish the public key. Both you and your intended recipient create public/private key pairs and send each other the public keys. To send a symmetric encryption key to your intended recipient, you encrypt the symmetric key with their public key (see Figure 3). They use their private key to be able to decrypt the symmetric key (see Figure 4).
 Asymmetric cryptography depends on the mathematical relationship between the public and private keys. For example, one technique used by asymmetric cryptography is to choose two large prime numbers as the private key and multiply them together to obtain the public key. The security of the private key is dependent on the difficulty of solving the mathematical problem of the public key, in this case factoring a very large number into its two primes. Experts estimate that modern public/private key systems would take billions of years to crack using the means at our disposal today.
Asymmetric cryptography depends on the mathematical relationship between the public and private keys. For example, one technique used by asymmetric cryptography is to choose two large prime numbers as the private key and multiply them together to obtain the public key. The security of the private key is dependent on the difficulty of solving the mathematical problem of the public key, in this case factoring a very large number into its two primes. Experts estimate that modern public/private key systems would take billions of years to crack using the means at our disposal today.
Quantum computing
The computers we’re familiar with use binary logic, where each unit of information, or bit, can have only one of two states. Quantum computing works with individual atoms which can have many different values and can have multiple states at once. The unit of quantum computing is the “quantum bit,” or qubit.
A Cryptographically Relevant Quantum Computer (CRQC) will be able to solve the difficult mathematical problems used by asymmetric cryptography in hours, minutes, or seconds rather than billions of years.

Quantum computer
A CRQC is estimated to be about 8192 qubits in size. This is well beyond the capability of current known quantum computers. Estimates vary substantially as to when a CRQC will be achieved, but the earliest current estimates put the date in 2029.
The era after the development of a CRQC is referred to as “Post-Quantum Cryptography,” or PQC. In the PQC era, asymmetric algorithms such as Diffie-Hellman and RSA will be ineffective at protecting information.
Some groups are already talking about a quantum version of Y2K that they’re calling Y2Q. I don’t agree with this. I think that in true quantum fashion, some aspects of PQC are already here, and some may not materialize for years.
One of the quantum threats is called “hack and store,” where networks are being compromised now and the captured information stored for future decryption when a CRQC is able to decrypt the key exchanges to obtain the keys to today’s network traffic. This is a real threat and should be considered when you think about the urgency of replacing current cryptographic processes with quantum-safe processes after they become available later in 2024. Below I offer some elements to consider when transitioning to this new quantum era.
Protecting our operational assets
You should consider these elements when formulating your plan to address the risks being introduced by quantum computing:
1. Determine what quantum-safe cryptography means to your organization.
This may consist simply of using the new NIST processes but may also include increasing symmetric cryptography key sizes or other actions that may be advisable based on NIST or other guidance.
2. Ensure any new acquisitions will be quantum-safe.
Update your procurement language for operational assets to require quantum-safe cryptography where cryptography is used. And incorporate testing for quantum-safe encryption in your Factory or Site Acceptance Testing (FAT/SAT).
3. Inventory all encrypted communications used in your operational environments.
As you do this, try to determine the useful life of the encrypted information so you know how vulnerable the information is to the “hack and store” attack. For example, real-time generation information may have little value in the future, but a network diagram will likely still be valid in a few years. Your inventory should determine what communications protocols are in use and what forms of encryption (if any) are used. Use internal network security monitoring (INSM) to identify at-risk communications within your Electronic Security Perimeters (ESPs) and within your assets containing low impact BES Cyber Systems. I suggest you do not wait for the INSM standard (CIP-015 as of this writing) to become enforceable. You need this information as soon as possible so you can plan a smooth transition to quantum-safe encryption. Use external monitoring techniques (firewall logs, etc.) to monitor applicable network traffic outside your ESP and between all your BES assets. Ensure your encrypted communication inventory includes:
• ICCP or other inter-Control-Center traffic per CIP-012,
• Interactive Remote Access,
• Communications to and within any Physical Access Control Systems,
• Communications to any Electronic Access Control or Monitoring Systems,
• Vendor communications,
• Authentication systems (Active Directory, etc.), and
• Cloud-based systems, if any.
4. Identify secure data storage systems, such as:
• BES Cyber System Information repositories,
• Password repositories, and
• Backup systems.
5. Identify other uses of encryption that may be affected, such as:
• Digital signatures, or
• Cryptographic hashes for verification of software authenticity.
6. Determine whether existing encryption is quantum-safe.
At the time of this writing, NIST considers AES-256 to be quantum-safe. As this is an emerging area, the guidance from NIST should be monitored on an ongoing basis and any changes considered in your plans.
7. Plan to update at-risk encryption to quantum-safe processes.
These update plans are probably going to be difficult to coordinate, both within your organization and with your communication partners. Also, note that both ends of an encrypted communication channel must be modified at the same time.
8. Monitor the state of quantum computing and accelerate or re-prioritize plans as needed.
It will be advisable to actively monitor the information and documents coming from NIST in the foreseeable future.
Conclusion
Once a sufficiently capable quantum computer is developed by a commercial organization, educational institution, or hostile nation-state, many of the forms of encryption we use in our operational assets will be at risk. We need to begin planning now to address this risk.
References
• NIST Post-Quantum Cryptography Project
• NIST Post-Quantum Cryptography References
• The Map of Quantum Computing – Quantum Computing Explained
• Cloud Security Alliance – Practical Preparations for the Post-Quantum World
Requests for Assistance
If you are an entity registered within the RF Region and believe you need assistance in sorting your way through this or any compliance related issue, remember RF has the Assist Visit program. Submit an Assist Visit Request via the RF website here.
Feedback
Please provide any feedback you may have on these articles. I may be reached at lew.folkerth@rfirst.org.

